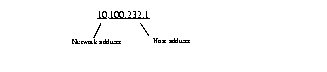
| 32-Bit Value | Dotted Decimal Notation |
|---|---|
| 01100100.01100100.01100100.00001010 | 100.100.100.10 |
| 11000011.00100000.00000100.11001000 | 195.32.4.200 |
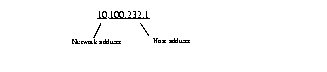
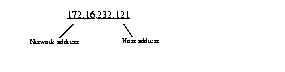
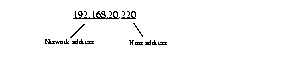
Note ¯ ![]() Do not assign an IP address with all 0s or all 1s in the host portion of the address to a host on the network, because these are reserved as broadcast addresses.
Do not assign an IP address with all 0s or all 1s in the host portion of the address to a host on the network, because these are reserved as broadcast addresses.
These 4 bytes (32 bits) specify on which network segment the node resides.
These 6 bytes (48 bits) provide the media access control (MAC) address of the node.
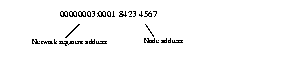
Command> set user-netmask on
Command> save all
Caution ¯ ![]() The VLSM feature affects both routing and proxy ARP on the PortMaster and must be used with caution.
The VLSM feature affects both routing and proxy ARP on the PortMaster and must be used with caution.
Note ¯ ![]() The internal host table should be used only when no other host mapping facility is available. Using the host table only when necessary reduces confusion and the amount of network maintenance required.
The internal host table should be used only when no other host mapping facility is available. Using the host table only when necessary reduces confusion and the amount of network maintenance required.